Figure 1:The Turing Way project illustration by Scriberia. Used under a CC-BY 4.0 licence. DOI: The Turing Way Community & Scriberia (2024).
Prerequisites¶
| Prerequisite | Importance | Skill Level | Notes |
|---|---|---|---|
| Sensitive Data Projects | Helpful | Beginner |
Summary¶
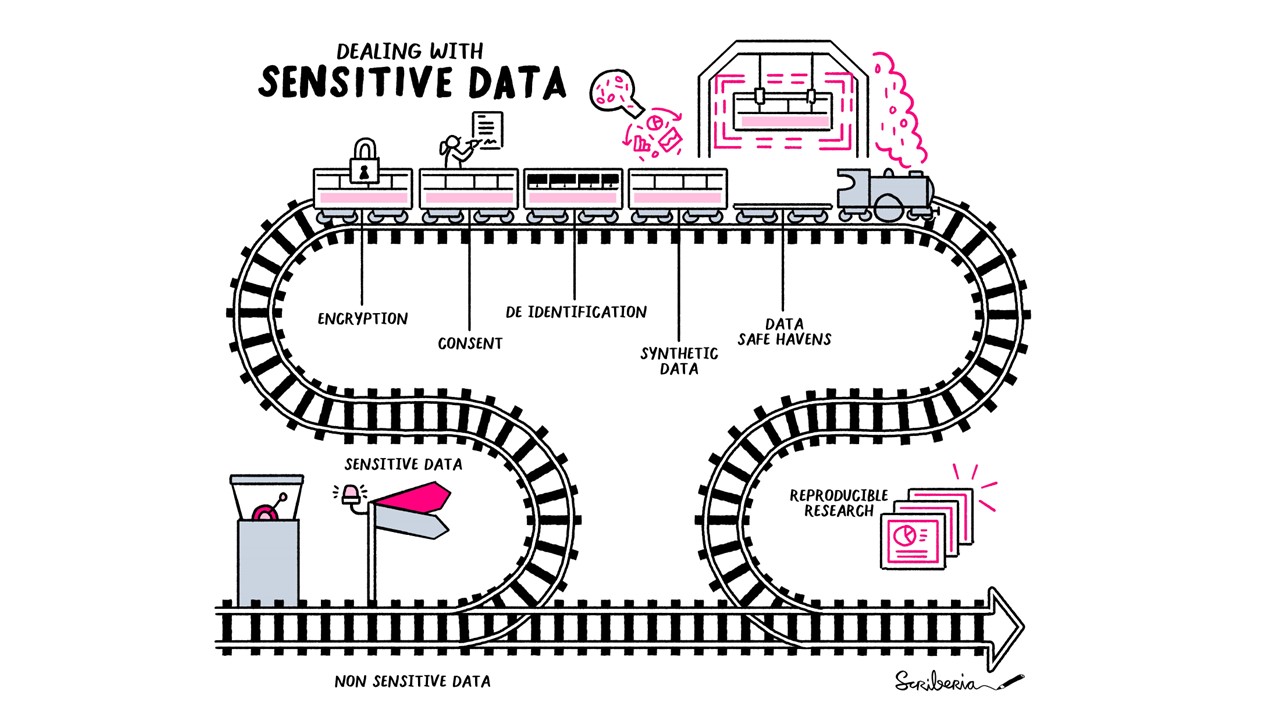
In this chapter, we describe specific ways that you can manage sensitive data.
This includes:
- Informed consent
- Data Privacy Strategies
- Sharing sensitive data
Motivation¶
Researchers need to conform to legal and ethical restrictions when working with sensitive data. There are many ways that you can do this and it will depend on the type of data that you are analysing.
- The Turing Way Community, & Scriberia. (2024). Illustrations from The Turing Way: Shared under CC-BY 4.0 for reuse. Zenodo. 10.5281/ZENODO.3332807